The equipment of Tiangong Technology can be widely used in various data recovery laboratories, data analysis institutions, education platforms, big data room, command and dispatch center, multimedia data center and many other scenarios. It is the designated data source recovery technology “efficiency source technologyâ€. Equipment appearance supplier. The following is the specific application of the "multi-function maintenance workstation ED-SP9600" in the efficiency source technology data recovery business.
Equipment Name: Multi-function maintenance workstation ED-SP9600
Function introduction: Multi-function maintenance workstation ED-SP9600, with unique dual-screen display, technology blue environment lighting, full metal texture combined design; a variety of data interfaces, can integrate a variety of data analysis and repair equipment on the market It is equipped with Japanese white welding station, hot air gun, BGA welding machine, etc., and completes all kinds of equipment maintenance and data processing work in one stop. Product design professional, strong sense of science and technology, image atmosphere and anti-static, anti-electric shock and so on. Widely used in laboratory repair stations, various types of electronic equipment maintenance, computer city data recovery, command center integrated computer.
Equipment pictures:

Editor's Note: In the first issue of "Technical Combat" "Mobile Data Extraction" series, the source of efficiency source scientific and technical personnel has completely presented the basic process and basic precautions of "mobile data extraction" through the data extraction of Root Android mobile phone. . In this issue, the data extraction of the mobile phone that has caused damage will be explained and introduced through actual cases. Because this case involves specific criminal cases, all sensitive information in the text is blurred.
Case Background: An unnamed corpse was found in the wilderness of a certain area of ​​Sichuan Province in the year of xxx. After investigation by the public security organs, a mobile phone was found in a puddle near the unknown body. The mobile phone has been soaked in water and filled with debris and other debris. In order to confirm the identity of the victim, the public security organ needs to extract the data information from the mobile phone.
Actual combat object: A brand of smart phone, the appearance is damaged, the mobile phone is soaked in water, there are debris and other debris inside.
Technical Analysis: Since the phone has been physically damaged, logical image extraction is not possible. The mobile phone must be disassembled and the chip removed, and then the image data of the chip content is obtained by accessing the mobile phone chip data reading device. Finally, through the mobile forensic tool SPF9139 data extraction and recovery of the image, get the key information of the mobile phone.
Extraction equipment: SCE9168 mobile phone chip data extraction system, SPF9139 mobile phone data recovery forensics system
The SCE9168 system consists of three parts: “Professional Mobile Phone Chip Removal Toolâ€, “Mobile Phone Chip Data Extraction Tool†and “Mobile Phone Chip Data Extraction Analysis Softwareâ€. Equipped with a variety of EMMC, EMPC chip readers, mainly used to solve the problem of direct extraction and analysis of data caused by corrosion, external damage, motherboard damage, water immersion, etc. of the smartphone hardware.
SPF9139 system is a mobile electronic forensics integrated equipment integrating physical mirroring, data recovery, data extraction, forensic analysis and other technologies. It has powerful system recovery, database file feature recovery, APP data recovery, file type recovery, keyword search. It can analyze the track and trail trajectory, generate forensic reports that meet the requirements of the judicial department, and support mainstream smartphones and some cottage phones such as Android, IOS and WP.

Figure 1: Integrated workstation with SCE9168 and SPF9139 systems
Extraction steps:
First, observe and test mobile phones
After getting the mobile phone, the efficiency source technician observed and detected that the mobile phone has been physically damaged and cannot be logically imaged.
Remarks: If the mobile phone is not damaged, you can directly connect to the SPF9139 system for physical mirroring and data extraction. For details of the operation process, please refer to the operation procedure of "Mobile Data Extraction Phase 1: Root Android Mobile Phone Normal Data Extraction Operation Case".

Figure 2: A damaged phone
Second, disassemble the mobile phone chip
In the efficiency source studio, the technician first cleans up the dirt, debris and other stains in the mobile phone, and then disassembles the mobile phone and disassembles the chip through the "professional mobile phone chip removal tool" provided by the SCE9168 system.
Remarks: During the process of disassembling the mobile phone chip, pay attention to whether the components around the heat gun are affected. For example, the Motorola L2000 mobile phone must remove the SIM card connector when disassembling the font, otherwise it will be easily blown. In addition, Motorola T2688, Samsung A188, Ericsson T28 amplifier and many soft-packaged fonts, these BGA-IC high temperature resistance is not good, the temperature is not too high when blowing, otherwise it will be vulnerable to damage to the device.

Figure 3: Removing the phone chip
Third, chip data mirroring
After disassembling the mobile phone chip, access the mobile phone chip data reading device in the SCE9168 system, obtain the image of the mobile phone chip content data through the physical mirroring function in the system, and verify the MD5 value.
Note: MD5 is simply a security policy. It can produce an equally unique "digital fingerprint" for any file (regardless of its size, format, number). If anyone makes any changes to the file, the MD5 value will be the corresponding "digital fingerprint". The MD5 value is checked to ensure the authenticity of the data of the mobile phone chip.
Figure 4: Physical image of the phone chip
Fourth, data extraction and recovery
After the mobile phone chip is physically mirrored, the physical image file is connected to the SPF9139 system for data extraction and recovery. After the physical image file is connected to the SPF9139 system, it can display mobile phone data such as basic information of the mobile phone, social chat, web trace, mainstream mailbox, and map bus. According to the needs of this case, select mobile phone contacts and text messages for extraction, and successfully obtain more than 130 mobile phone contacts and more than 10 text messages.
Figure 5: Select contacts and text messages for extraction
Figure 6: Extracted SMS message
Figure 7: Extracted contact information
V. Key information retrieval
In order to provide more useful information and clues to the case, the efficiency source technicians passed the SPF9139 system.
Further searching for the image data of the mobile phone chip, and successfully recovering the encoded information such as the IMSI and SIMID of the mobile phone.
Remark: The IMSI code refers to the international mobile subscriber identity code, which is a logo that distinguishes mobile users and is stored in the SIM card and can be used to distinguish the valid information of the mobile subscriber. The SIMID code refers to the ID and authentication authority of the corresponding number of the SIN card of the mobile phone. After the mobile phone is turned on, the ID in the card is used to log in to the network. Obtaining the IMSI and SIMID codes of mobile phones is of great significance for identifying the identity of mobile phone users.
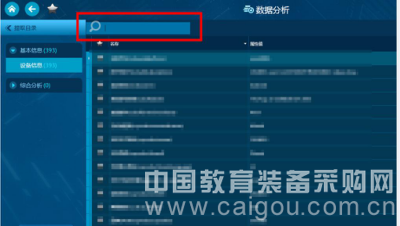
Figure 8: Key Information Search
6. Export data analysis report
After analyzing the extracted data, the corresponding extracted data information can be generated into an analysis report according to the needs of the case, and the results of the data extraction are fully presented for the case to be detected or forensic.
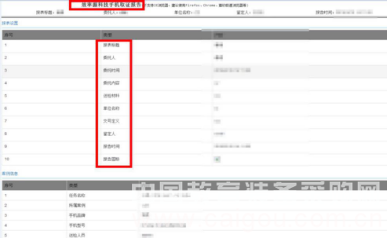
Figure 9: Generating a report
Extraction results: Through the above six steps, the efficiency source technicians extracted the contact information, SMS, IMSI, SIMID and other information and data in the damaged mobile phone, providing key information and clues for the victim identification and case detection.
[Editor's post: In the process of electronic forensics and judicial appraisal by the public security and judicial departments, it is often the case that mobile phone damage cannot be directly extracted. Through this case, we can see that the efficiency source SCE9168 and SPF9139 systems can mirror the data of the mobile phone chip, extract and analyze the key data in the mobile phone, and provide key information for case detection. About how to do non-ROOT extraction of Android phones, IOS jailbreak extraction, IOS non-jailbreak extraction, bypassing Android screen locks, ROOT permissions, etc. will be presented to you in future cases, so stay tuned!]

Tinted Aluminum Mirror,Tinted Aluminum Mirror Uv,Tinted Aluminum Mirror Tint,Tinted Aluminum Mirror Reflector
Dongguan Huahui Glass Manufacturing Co.,Ltd , https://www.antiquemirrorsupplier.com